5.4 Configure, verify, and troubleshoot basic device hardening | CCNA Packet Tracer RIP Lab part 2 - YouTube

Cisco Device Hardening Disabling Unused Cisco Router Network Services and Interfaces. - ppt download
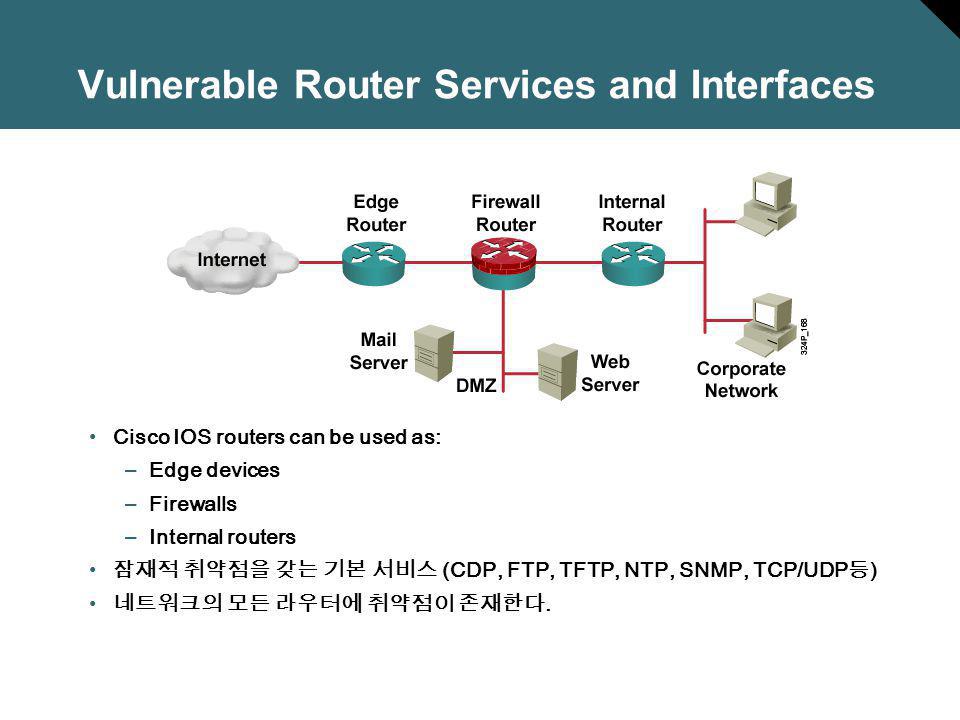
Cisco Device Hardening Disabling Unused Cisco Router Network Services and Interfaces. - ppt download
PDF) Hardening CISCO Devices Based on Cryptography and Security Protocols - Part One: Background Theory